
Vulnerability detection
From vulnerability detection to vulnerability management
Vulnerability detection provides organizations with insight into weaknesses within their environment, enabling them to pinpoint systems, applications, or configurations that require remediation or improvement.
That insight becomes most valuable when vulnerability detection is part of a broader vulnerability management approach. This is where visibility turns into priorities and priorities turn into action.
For CISOs, the core question remains simple:
Where are our weak spots, and which ones are they?
Detection provides the information needed to answer that question. Vulnerability management ensures those findings are tracked, monitored, and maintained over time.
Vulnerability detection as part of a broader process
Vulnerability detection doesn’t stand on its own. It sits inside a broader vulnerability management process that continues over time.
You detect vulnerabilities, assess them, decide on next steps, address what you can, manage remaining risks, and revisit those decisions as environments change. New vulnerabilities appear, software changes, configurations shift, and updates introduce new considerations.
However, this process is not static; it is continuous and constantly evolving. Detection delivers raw input and vulnerability management turns that input into decisions.
Context and risk-based prioritisation
Here’s where many teams run into challenges.
Vulnerability tools often produce large numbers of findings, many of them labelled as high or critical. From a risk analysis perspective, those labels are a starting point, not a conclusion.
A risk-based approach helps put findings into context. It looks beyond severity scores and considers how a vulnerability could be exploited, where it exists in the environment, and how it relates to business processes.
Some findings appear severe but have limited practical impact. Others may look less prominent yet deserve immediate attention because of their role in the organisation. Context is what makes that difference.
Companies should then prioritize risk-based approaches which brings focus and helps teams decide where to start.
Tools support the process, people guide the outcome
There’s a familiar message in the market: install a tool, switch it on, and security improves automatically.
In practice, tools work best when they support a clear process and are combined with expertise. They need configuration, tuning, and interpretation to provide meaningful insight.
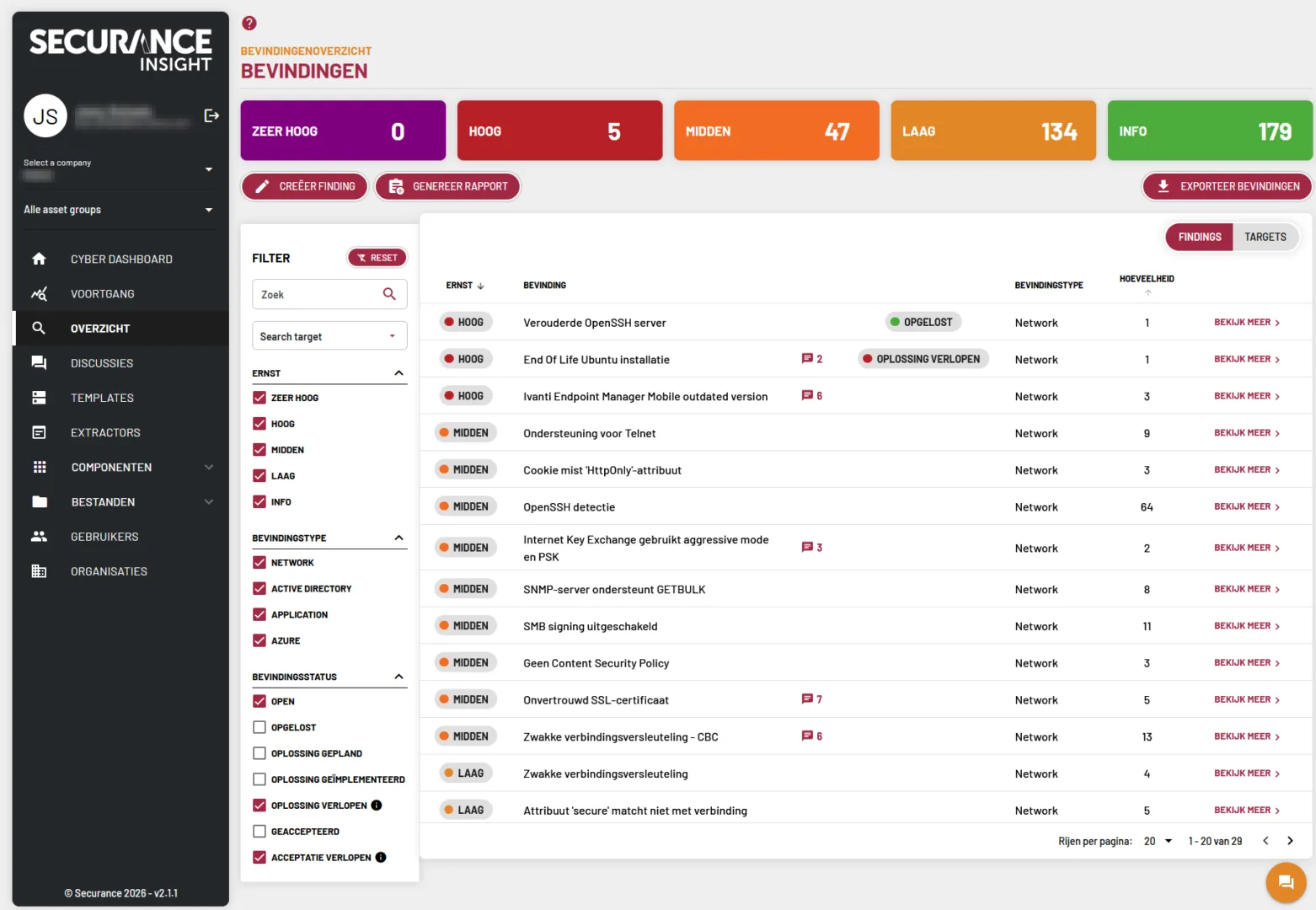
At Securance, tools are part of the setup, not the end goal. Our Insight dashboard brings vulnerability data together so customers can manage findings, support risk-based prioritisation, track remediation, and document risk acceptance over time.
Insight supports the process. Expertise guides the decisions.
Why a familiar point of contact matters
What customers often value most is having a point of contact who knows their environment and understands their setup. Someone who can explain what deserves attention now and what can be managed over time.
That personal connection helps translate vulnerability detection into concrete action. It supports consistent decision-making and keeps the focus on what matters most from a risk perspective.
The business perspective
Security outcomes are difficult to quantify because the incidents that are prevented rarely become visible.
Still, one reference point helps frame the conversation. Ransomware payments typically fall in the range of 1–2% of annual revenue. For a company with €100 million in revenue, that can mean up to €2 million. For a €55 million organisation, roughly €1 million.
From a business point of view, vulnerability management supports risk reduction by limiting the potential impact of security incidents.
A practical improvement that makes a difference
One of the most effective improvements organisations can make is sharpening how they prioritise vulnerabilities.
A risk-based view helps distinguish between findings that require immediate action and those that can be addressed over time. It shifts attention from volume to relevance.
Those decisions rely on context, experience, and a solid understanding of both the environment and the business.
That’s where vulnerability detection delivers its full value: as part of a structured, expert-led vulnerability management process.
