Benefits of High Level Structure
There is often discussion about High Level Structure (HLS) in ISO standards. But what does this entail? What are the requirements that a company must meet, and what are the benefits of HLS for ISO standards?
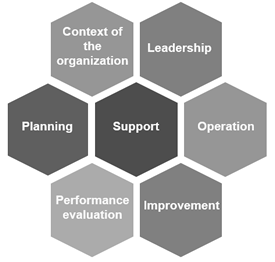
The new ISO standards we know today are based on the HLS structure. HLS can be described as a universal standard for management system standards, enabling integrated business management. For every company, information security is crucial. The ISO 27001 standard is an international framework for information security. ISO 27001 can be used to implement information security measures. In 2017, the latest ISO 27001 standard was published. This standard is based on the HLS structure. HLS stands for High Level Structure and refers to the initiative to develop a ‘structure on main lines’ for management system standards. The HLS structure is based on the plug-in model. This plug-in model is ISO’s response to market demands to ensure that management system standards are interconnected and logically related.
HLS
The new ISO standards are easier to integrate through the High Level Structure. What makes HLS ideal is that a single basic system needs to be established, and from here, different standards can be “plugged in.” There are several requirements that an organization must meet for the implementation of HLS.
- Risk management
- Leadership
- Compliance management (also necessary for an ISO standard)
- Demonstrability
- Improvement management
Benefits of HLS in the Organization
As described, the HLS system makes it increasingly easier to implement different ISO standards within the organization. This ensures that management system standards are interconnected and logically related. From here, the needs of stakeholders are central. HLS ensures that the organization’s management takes a more direct role and is more involved in implementing the management system.
Securance offers services in governance, risk, and compliance. Securance has been the market leader in the Netherlands and the most progressive organization in ISAE 3402 implementation and certification. We offer services in ISAE 3000, GDPR/AVG, ISO 27001, ISO 9001, and COSO ERM, in addition to ISAE 3402.





