What is SOC 2 and what are the benefits?
The number of organizations managing customer data is increasing, leading to a growing demand for SOC 2 reports that assess the adequacy of information security measures in place. IT companies are now expected to be SOC 2 compliant, particularly when storing data in the cloud.
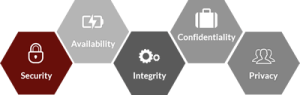
SOC 2 compliance means that an organization has implemented strict procedures for information security, privacy protection, and other areas, depending on the scope of the SOC 2 report. The scope is defined by the American Institute of Certified Public Accountants (AICPA) Trust Service Criteria (TSCs), which cover information security (1), system availability (2), process integrity (3), confidentiality (4), and privacy (5). Organizations can choose which principles to comply with, but information security must be included.
What is a SOC 2 report?
A SOC 2 report outlines the TSCs in terms of control measures and a description of the overall risk management system. An external auditor verifies that the description matches reality, and upon approval, provides an assurance statement for the SOC 2 report.
Why is SOC 2 in high demand?
Organizations must demonstrate to their clients that they adequately secure data. This involves implementing a risk management system and ensuring that their vendors also manage risks effectively. Clients demand evidence of this, which can be provided through SOC 2 compliance.
Benefits of a SOC 2 report
- Organizations use SOC 2 reports as a marketing tool, assuring new and existing clients of their reliability.
- Implementing SOC 2 positively impacts the quality of risk management.
- Clients gain confidence that risks are effectively managed.
- IT inquiries from partners and clients can be answered more efficiently.
- Opportunities arise to attract and retain clients.
Advantage in procurement
During the sales process, clients often ask vendors to complete an IT questionnaire prepared by their engineering team. A SOC 2 report can effectively answer these questions, streamlining the process and instilling confidence in the client that processes are well-managed.
SOC 2 and the cloud
As demand for cloud-based solutions grows, SOC 2 certification becomes increasingly important. A SOC 2 report is seen as the industry standard that distinguishes an IT solutions provider from its competitors. If your organization aims to stand out, contact one of our consultants.
Get started with SOC 2
Are you prepared to demonstrate your commitment to robust information security and data privacy practices through SOC 2 compliance? Securance offers comprehensive SOC 2 auditing services to guide you through this rigorous certification process. Our experienced auditors will conduct a thorough assessment of your controls against the SOC 2 Trust Services Criteria, providing a detailed report and recommendations to achieve full compliance. Contact Securance today to embark on your SOC 2 journey and gain a competitive edge by instilling confidence in your clients.