A vulnerability scan, penetration test (pentest) and Red Teaming are different ways to test cybersecurity. The terms are often confused or misused. Do you know which test best fits your needs? In this blog post, we will cover the difference between red teaming vs penetration testing vs vulnerability scanning.
Red teaming vs penetration testing vs vulnerability scanning in brief
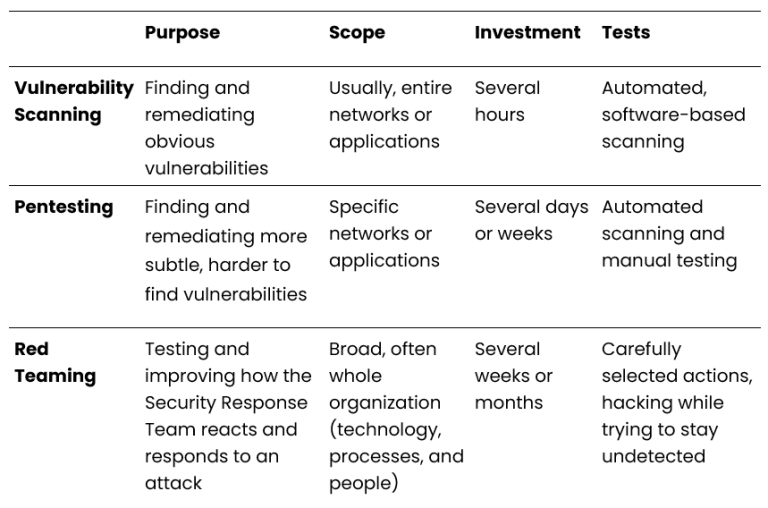
Vulnerability Scanning
In a vulnerability scan, we examine an IT system or network for vulnerabilities. In this way we make possible targets visible, for example software that has not been updated on time or settings that are not secure. The results of a vulnerability scan provide an overview of the weaknesses in your organisation’s IT system.
At Securance, we scan with Nessus, Tenable’s vulnerability scanner. You can choose to have your external or internal network scanned. After the scan, one of our ethical hackers reviews whether the vulnerabilities found are false positives. With a false positive, the scan indicates that a vulnerability has been found, while this is not the case. At the end you get a scan report or you can see the results in a dashboard. We help you interpret and resolve the scan results. We do the scanning for free for our customers who have a pentest subscription.
Penetration Testing (pentest)
In a pentest, we also examine your IT system or network for vulnerabilities. But a pentest goes a step further than a vulnerability scan by testing the vulnerabilities found. We break into your IT environment, giving you a better picture of the vulnerabilities and risks in your applications, systems and networks.
Before we begin a pentest, we agree on what you want tested, for example, the systems directly connected to the Internet, the internal infrastructure, the Windows domain, a website, or web application. We also discuss how long the test will take and what access we will have.
In a comprehensive pentest (ransomware vulnerability analysis), we perform at least the following tests:
- Phishing test
- External infrastructure test
- Internal network test
- Windows domain test
- Cloud configuration review
- Workstation test
- Wi-Fi test
Upon completion of the pentest, we will write a report on the findings and discuss the results. This allows you to take targeted measures to reduce your risks and improve your security.
Red Teaming
During red teaming, our hackers behave as much as possible like real attackers. The purpose of red teaming is to test an organisation’s defenses against a targeted attack and to see how the organisation responds. While performing the test, the red team tries to remain undetected. Your organisation’s defensive group is called the blue team. This team monitors all systems and responds to incidents.
A red team tests not only the technical security of your system, but also the response of the organisation’s personnel and one defends against an attack. The team tries to circumvent security measures by exploiting weaknesses in the company’s systems, processes and personnel.
Before we begin, we discuss the scope, duration and purpose of the assignment. Upon completion of the test, we discuss whether and how the goal was met and what attacks we used to do so. We compare these actions with the attacks noticed by the blue team. In a comprehensive report, we share our findings and recommendations for improving security.
What do I choose?
Now you have a broad understanding of red teaming vs penetration testing vs vulnerability scanning, but what do you choose within your organization?
The best test depends on your organisation’s purpose and situation. Do you want a broad understanding of the vulnerabilities within your IT system? Then a vulnerability scan is a good choice. It gives a first impression and can help you resolve the most notable vulnerabilities immediately.
Where a vulnerability scan ends, a pentest continues. During pentesting, an ethical hacker goes to see if vulnerabilities are attackable. A pentest is especially suitable when you want to have a specific system or network tested in detail. This allows you to know exactly where the most risks lie.
If you want to know how well your organisation responds to a cyberattack (identify, detect, protect, recover), then you should opt for red teaming. This is the next step if you have already had multiple pentests performed and no high risks or vulnerabilities come out of them.
Want to have your organisation tested?
Would you like to have a vulnerability scan, pentest or red team assignment performed? Or do you have any questions? Call the experts at Securance HackDefense at phone number (+31) 71 204 0101 or send an email to cyber@securance.com. We would be happy to help you!



